Inspired by a post by John Lambert and others who contributed, I’ve put together a table of Base64 encodings for certain file signatures and script elements often encountered in malware analysis.
Due to the nature of Base64 encoding, there are different possibilities of the encoding result depending on the placement of the bytes in the overall structure of the blob. Using CyberChef all the possible Base64 offsets can be determined. However, in the below tables for ease I’ve only included the fixed bytes as if the header was at the start of the blob of Base64.
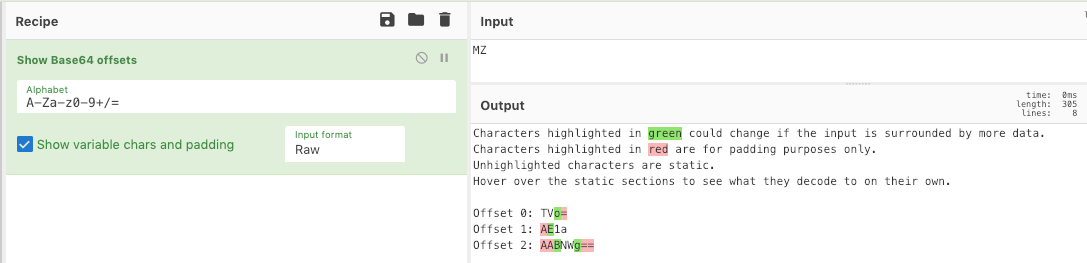
For those files that don’t have a readable signature, this simple CyberChef recipe will change the hex values to display their Base64 offsets.
![[base64_hex_header]](/2019/02/base64_hex_header.png)
File Signatures
File signatures, aka ‘magic bytes’ or ‘file headers’, are static bytes that appear at the start of files.
Common Script Elements
These script elements are common leading commands that can be encountered during script analysis.
This post was essentially to save a series of Tweets that I found useful. It is not complete and if you want to add further entries please let me know at [email protected] or @mattnotmax
References:
File headers: https://www.garykessler.net/library/file_sigs.html Refinement of RTF signature: @decalage2
